Wireless Local Area Networks (WLANs): Difference between revisions
No edit summary |
No edit summary |
||
| Line 7: | Line 7: | ||
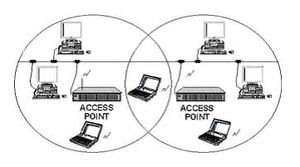
<br>In a centrally controlled network, a network administrator has set up an access point to a high-speed network hub. In a typical business office WLAN system, the controlling wireless unit is normally mounted in a central hallway and is called an Access Point (AP) radio. Several of these APs are usually located in a building to give good coverage to all offices. This same concept applies to a home network where one access point is usually sufficient. A centrally controlled access point radio is connected to a high data rate wired Local Area Network (LAN) that can take the data from many computers to a centrally located server computer and then on to the Internet. | <br>In a centrally controlled network, a network administrator has set up an access point to a high-speed network hub. In a typical business office WLAN system, the controlling wireless unit is normally mounted in a central hallway and is called an Access Point (AP) radio. Several of these APs are usually located in a building to give good coverage to all offices. This same concept applies to a home network where one access point is usually sufficient. A centrally controlled access point radio is connected to a high data rate wired Local Area Network (LAN) that can take the data from many computers to a centrally located server computer and then on to the Internet. | ||
[[Image:WLAN2.jpg|thumb]] | [[Image:WLAN2.jpg|thumb]] | ||
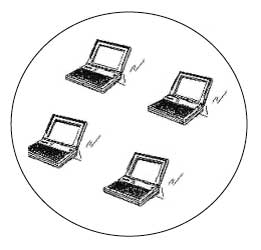
A peer-to-peer network is used in more isolated instances, such as when two users want to link privately or there is no network access point. There is also a second kind of wireless network that is sometimes used, which is called a “mesh” or “peer-to-peer” network. In this kind of network, computer devices communicate directly to each other without passing information through the central access point. In a centrally controlled network, WLAN radios operate at a radio frequency of 2.4 GHz or 2.4 billion cycles per second. There are additional frequencies at 5 GHz where high data rate WLAN operates. Other devices, like [[Microwave Ovens|microwave ovens]], operate at the same frequencies but special care has been used to keep interference from these devices to a minimum and get data through to other computers. | |||
At the present time laptop computers are the main users of WLANs. In the future, however, more items will incorporate WLAN technology to communicate. For example, personal digital assistants (PDAs), cameras, appliances and other everyday objects on the evolutionary horizon will increasingly rely on WLAN technology. | At the present time laptop computers are the main users of WLANs. In the future, however, more items will incorporate WLAN technology to communicate. For example, personal digital assistants (PDAs), cameras, appliances and other everyday objects on the evolutionary horizon will increasingly rely on WLAN technology. | ||
| Line 13: | Line 15: | ||
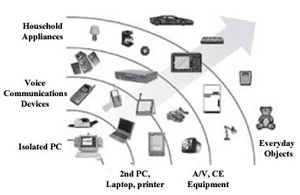
[[Image:WLAN3.jpg|thumb]] <br>In the future items such as PDAs, cameras, appliances, and everyday objects, will use WLAN technology to communicate. <br>An important issue in a WLAN is security, as wireless networks are potentially more vulnerable than their wired counterparts to external interception. Encryption of data is one way security is enhanced. The WLAN standard, IEEE Std 802.11, (that’s the document that sets the procedures for setting up a WLAN) incorporates private-key cryptography and uses a challenge and response random message that confirms the integrity of any mobile computer. There are several major types of operations permitted in IEEE Std 802.11. Two of the most interesting are frequency hopping radio and spread spectrum radio. Frequency hopping radio changes the frequency very quickly to avoid any interference. For example, if a microwave oven is on your WLAN frequency the radio will quickly hop to a new frequency and leave the interference behind. Spread spectrum radio widens the signal and is also able to avoid interference from other radios. These two operations will help ensure the continued growth of WLAN technology and the proliferation of wireless devices.<br><br> | [[Image:WLAN3.jpg|thumb]] <br>In the future items such as PDAs, cameras, appliances, and everyday objects, will use WLAN technology to communicate. <br>An important issue in a WLAN is security, as wireless networks are potentially more vulnerable than their wired counterparts to external interception. Encryption of data is one way security is enhanced. The WLAN standard, IEEE Std 802.11, (that’s the document that sets the procedures for setting up a WLAN) incorporates private-key cryptography and uses a challenge and response random message that confirms the integrity of any mobile computer. There are several major types of operations permitted in IEEE Std 802.11. Two of the most interesting are frequency hopping radio and spread spectrum radio. Frequency hopping radio changes the frequency very quickly to avoid any interference. For example, if a microwave oven is on your WLAN frequency the radio will quickly hop to a new frequency and leave the interference behind. Spread spectrum radio widens the signal and is also able to avoid interference from other radios. These two operations will help ensure the continued growth of WLAN technology and the proliferation of wireless devices.<br><br> | ||
[[Category:Computers_and_information_processing]] [[Category:Computer_networks]] [[Category:Wide_area_networks]] | [[Category:Computers_and_information_processing]] [[Category:Computer_networks]] [[Category:Wide_area_networks]] [[Category:Power,_energy_&_industry_application|Category:Power,_energy_&_industry_application]] [[Category:Inspection,_safety_&_security|Category:Inspection,_safety_&_security]] [[Category:Cryptography]] | ||
[[Category:Power | |||
[[Category:Inspection | |||
[[Category:Cryptography]] | |||
Revision as of 15:20, 28 January 2009
Wireless Local Area Networks (WLANs)
When the first personal computers appeared in the late 1970s, they were meant to be placed on a desk. However, with the advent of laptop computers in the 1980s, and handheld computers in the 1990s, people began using these devices in airplanes, automobiles, or outside. This new mobility presented new problems when the Internet became widely used in the mid-1990s. People wanted to access the Internet wherever they were. As a solution, engineers proposed connecting computers to the Internet through a wireless radio link rather than ordinary wires—a Wireless Local Area Network or WLAN. WLANs, which use microwave radio, have a mobile station and at least one fixed station that connects all mobile laptops within a network. WLANs have become so successful that today they are installed in offices to allow workers to carry their computers from place to place inside buildings. WLANs are also being installed on college campuses to allow students and faculty to freely move about with their computers, and in homes to avoid costly and unsightly network wires in walls.
In a centrally controlled network, a network administrator has set up an access point to a high-speed network hub. In a typical business office WLAN system, the controlling wireless unit is normally mounted in a central hallway and is called an Access Point (AP) radio. Several of these APs are usually located in a building to give good coverage to all offices. This same concept applies to a home network where one access point is usually sufficient. A centrally controlled access point radio is connected to a high data rate wired Local Area Network (LAN) that can take the data from many computers to a centrally located server computer and then on to the Internet.
A peer-to-peer network is used in more isolated instances, such as when two users want to link privately or there is no network access point. There is also a second kind of wireless network that is sometimes used, which is called a “mesh” or “peer-to-peer” network. In this kind of network, computer devices communicate directly to each other without passing information through the central access point. In a centrally controlled network, WLAN radios operate at a radio frequency of 2.4 GHz or 2.4 billion cycles per second. There are additional frequencies at 5 GHz where high data rate WLAN operates. Other devices, like microwave ovens, operate at the same frequencies but special care has been used to keep interference from these devices to a minimum and get data through to other computers.
At the present time laptop computers are the main users of WLANs. In the future, however, more items will incorporate WLAN technology to communicate. For example, personal digital assistants (PDAs), cameras, appliances and other everyday objects on the evolutionary horizon will increasingly rely on WLAN technology.
In the future items such as PDAs, cameras, appliances, and everyday objects, will use WLAN technology to communicate.
An important issue in a WLAN is security, as wireless networks are potentially more vulnerable than their wired counterparts to external interception. Encryption of data is one way security is enhanced. The WLAN standard, IEEE Std 802.11, (that’s the document that sets the procedures for setting up a WLAN) incorporates private-key cryptography and uses a challenge and response random message that confirms the integrity of any mobile computer. There are several major types of operations permitted in IEEE Std 802.11. Two of the most interesting are frequency hopping radio and spread spectrum radio. Frequency hopping radio changes the frequency very quickly to avoid any interference. For example, if a microwave oven is on your WLAN frequency the radio will quickly hop to a new frequency and leave the interference behind. Spread spectrum radio widens the signal and is also able to avoid interference from other radios. These two operations will help ensure the continued growth of WLAN technology and the proliferation of wireless devices.